A new report from cybersecurity firm Kaspersky Labs examining the targets — and intended effects — of this week’s massive malware attack comes up with some significant insights.
The attack, initially believed to be a variation of commercial malware software known as Petya, appeared to be a vast ransomware scheme. As the story developed, it became clear that the attack was more destructive than it was lucrative, as ransom payments failed to result in a return of decryption keys that would unlock affected systems.
Furthermore, at the time of writing, the attack has only generated just over 3.99 BTC — only about $10,300. Meanwhile, large-scale paralysis froze operations at major airports, banks and even Chernobyl’s radiation monitoring system. More than 60 percent of systems affected by apparent ransomware were located in Ukraine.
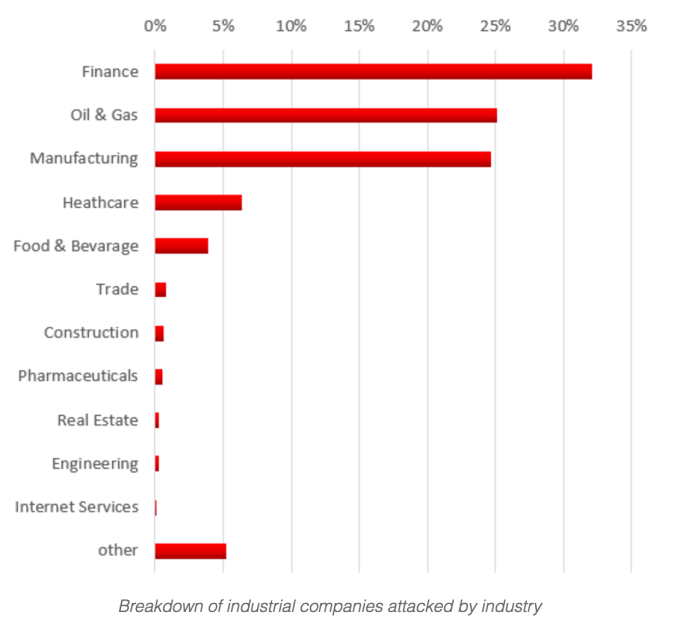
Now, Kaspersky Labs reports that while the finance sector was hit hardest, more than 50 percent of the remaining targets fell into the categories of manufacturing or oil and gas.
“This supports the theory that this malware campaign was not designed as a ransomware attack for financial gain,” Kaspersky Labs wrote in a blog analysis. “Instead, it appears it was designed as a wiper pretending to be ransomware.”
As Kaspersky’s blog post explains:
Join 10k+ tech and VC leaders for growth and connections at Disrupt 2025
Netflix, Box, a16z, ElevenLabs, Wayve, Hugging Face, Elad Gil, Vinod Khosla — just some of the 250+ heavy hitters leading 200+ sessions designed to deliver the insights that fuel startup growth and sharpen your edge. Don’t miss the 20th anniversary of TechCrunch, and a chance to learn from the top voices in tech. Grab your ticket before doors open to save up to $444.
Join 10k+ tech and VC leaders for growth and connections at Disrupt 2025
Netflix, Box, a16z, ElevenLabs, Wayve, Hugging Face, Elad Gil, Vinod Khosla — just some of the 250+ heavy hitters leading 200+ sessions designed to deliver the insights that fuel startup growth and sharpen your edge. Don’t miss a chance to learn from the top voices in tech. Grab your ticket before doors open to save up to $444.
Threats like ExPetr (Petya) are extremely dangerous for critical infrastructures and industrial companies because the attack can potentially impact the victim’s technological process automation/control systems. Such an attack could affect not only business production and finances, but also human safety.
According to our telemetry, we see evidence that many industrial companies are being attacked by ExPetr (Petya) malware. While there were examples of actual industrial control systems being affected, in most cases it was only the business networks that were affected.
There is plenty of debate over what to call the malware, but for now Kaspersky and others are calling it “ExPetr” to differentiate it from PetrWrap, a modification of the well-known Petya ransomware. Researchers at McAfee have also expressed skepticism that the malware is related to Petya: “Honestly there are similarities to Petya, but equally there are deviations as well,” McAfee Chief Scientist Raj Samani told TechCrunch earlier this week.
It’s still early days for any conclusive analysis about the ransomware formerly known as Petya, but suffice it to say the plot is thickening.


