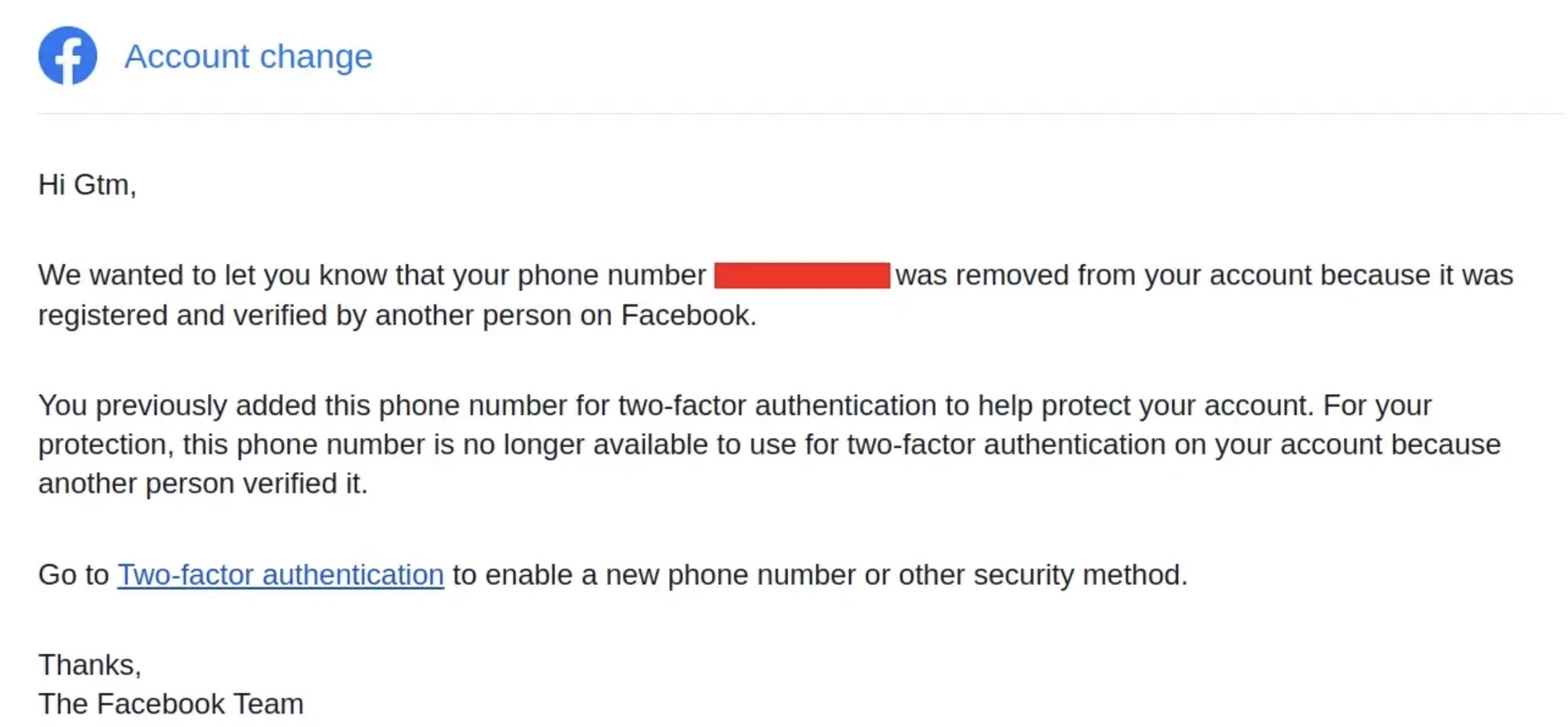
A bug in a new centralized system that Meta created for users to manage their logins for Facebook and Instagram could have allowed malicious hackers to switch off an account’s two-factor protections just by knowing their phone number.
Gtm Mänôz, a security researcher from Nepal, realized that Meta did not set up a limit of attempts when a user entered the two-factor code used to log into their accounts on the new Meta Accounts Center, which helps users link all their Meta accounts, such as Facebook and Instagram.
With a victim’s phone number, an attacker would go to the centralized accounts center, enter the phone number of the victim, link that number to their own Facebook account, and then brute force the two-factor SMS code. This was the key step, because there was no upper limit to the amount of attempts someone could make.
Once the attacker got the code right, the victim’s phone number became linked to the attacker’s Facebook account. A successful attack would still result in Meta sending a message to the victim, saying their two-factor was disabled as their phone number got linked to someone else’s account.
“Basically the highest impact here was revoking anyone’s SMS-based 2FA just knowing the phone number,” Mänôz told TechCrunch.
At this point, theoretically, an attacker could try to take over the victim’s Facebook account just by phishing for the password, given that the target didn’t have two-factor enabled anymore.
Mänôz found the bug in the Meta Accounts Center last year, and reported it to the company in mid-September. Meta fixed the bug a few days later, and paid Mänôz $27,200 for reporting the bug.
Join 10k+ tech and VC leaders for growth and connections at Disrupt 2025
Netflix, Box, a16z, ElevenLabs, Wayve, Hugging Face, Elad Gil, Vinod Khosla — just some of the 250+ heavy hitters leading 200+ sessions designed to deliver the insights that fuel startup growth and sharpen your edge. Don’t miss the 20th anniversary of TechCrunch, and a chance to learn from the top voices in tech. Grab your ticket before doors open to save up to $444.
Join 10k+ tech and VC leaders for growth and connections at Disrupt 2025
Netflix, Box, a16z, ElevenLabs, Wayve, Hugging Face, Elad Gil, Vinod Khosla — just some of the 250+ heavy hitters leading 200+ sessions designed to deliver the insights that fuel startup growth and sharpen your edge. Don’t miss a chance to learn from the top voices in tech. Grab your ticket before doors open to save up to $444.
Meta spokesperson Gabby Curtis told TechCrunch that at the time of the bug the login system was still at the stage of a small public test. Curtis also said that Meta’s investigation after the bug was reported found that there was no evidence of exploitation in the wild, and that Meta saw no spike in usage of that particular feature, which would signal the fact that no one was abusing it.
January 30: Headline updated to reflect that only Facebook accounts were vulnerable to the bug; this was due to an editing error. ZW.
Updated with comment from Meta.
Facebook is making two-factor mandatory for high-risk accounts


